Many resources compare GraphQL to RESTful APIs, often focusing predominantly on the functional aspects underlying both paradigms. Understandably, functionality is a key focus since some application scenarios logically require one over the other.
For instance, GraphQL excels in situations that require custom queries and efficient data fetching, making it ideal for applications with dynamic data needs. Predictability and a single endpoint simplify API consumption and integration. REST, on the other hand, remains a robust choice for applications where caching, established security practices, and hypermedia constraints are crucial. Its mature ecosystem and widespread use provide a wealth of tools and best practices, making it a reliable option for many projects.
However, the comparison between GraphQL and REST APIs should extend beyond functional aspects when it comes to building web applications. Each of these paradigms bears its unique impact on a company's security strategy due to the specific security-related advantages and challenges each offers. While both paradigms are essential tools for fetching and manipulating data, they have distinct approaches, strengths, and security considerations. Understanding these differences can help you make an informed decision for your next project and better estimate your cybersecurity expenditures.
Architectural Differences and Their Security Implications
Both RESTful APIs and GraphQL have unique architectural features that influence their security implications.
REST (Representational State Transfer) has been the cornerstone of web API design for many years. Its architecture is based on a set of well-defined principles: statelessness, resource identification through URIs, and a uniform interface using standard HTTP methods (GET, POST, PUT, and DELETE).
All notable advantages of the REST paradigm from a security standpoint begin with its tried-and-true status. REST's long-standing presence has led to a mature ecosystem of tools and libraries for implementing security measures like rate limiting, input validation, and OAuth authentication.
Other benefits, such as the clear separation of operations using HTTP methods (e.g., GET for fetching data, POST for creating resources), allow for straightforward access control implementation. Different security policies can be applied to different methods, enhancing granularity in permission settings. A notable quality of the REST APIs is their statelessness. Each request from a client to a server must contain all the information needed to understand and process the request. [] This statelessness simplifies the server design and can improve scalability and robustness. From a security perspective, it means that each request can be independently authenticated and authorised.
GraphQL, on the other hand, offers flexibility and efficient and tailored responses, which are among its primary advantages and disadvantages from a security standpoint. A prominent advantage of GraphQL is the precise data fetching it offers. This means that clients can request only the necessary fields, reducing the risk of exposing unnecessary data. This subsequently minimises the attack surface and can help enforce the principle of least privilege.
Furthermore, unlike REST, which often has multiple endpoints, GraphQL typically operates through a single endpoint. This can simplify authentication and authorisation mechanisms, as there is only one entry point to secure. Moreover, GraphQL schemas define a clear and strongly typed structure for data, which can aid in validating and sanitising inputs. This can help prevent common vulnerabilities like injection attacks.
However, all of these architectural-based benefits have unique security implications, which we will discuss in a comparative manner below. For a deeper dive into common security vulnerabilities in GraphQL-based web applications, refer to WeakLink Security’s dedicated white paper, which can be requested by the form in the end of this article.
API Endpoint Management
API endpoint management focuses on how different operations and data are accessed and controlled through specific endpoints. Effective endpoint management ensures that APIs are both efficient and secure, allowing for seamless communication between different systems while protecting sensitive information from unauthorised access.
| RESTful APIs | GraphQL |
|---|---|
| Multiple Endpoints. RESTful APIs typically use different endpoints for various operations. Each resource has a unique endpoint, such as /users for user data and /products for product data. | Single Endpoint. GraphQL operates through a single endpoint, handling all requests via a unified interface. This consolidation simplifies API consumption but complicates security, as all queries are processed through one entry point. |
| HTTP Methods. RESTful APIs rely on HTTP methods (GET, POST, PUT, and DELETE) to perform CRUD operations. This clear mapping facilitates straightforward access control based on endpoints and methods. | Queries and Mutations. GraphQL distinguishes between read-only queries and write-based mutations managed through the same endpoint. This requires nuanced authorisation mechanisms to ensure secure data access. |
For RESTful APIs, the segregation of endpoints allows for a more straightforward implementation of access controls and security measures tailored to specific resources. In contrast, GraphQL’s single endpoint necessitates robust, granular authorisation checks within the API logic to prevent unauthorised access and data leaks.
Data Fetching and Exposure
Data fetching and exposure are aspects of API design that determine how efficiently and securely data is retrieved and shared between systems. Efficient data fetching is essential for delivering a responsive user experience and minimising resource consumption on both the client and server sides. Different API architectures, notably RESTful APIs and GraphQL, offer distinct approaches to data fetching.
| RESTful APIs | GraphQL |
|---|---|
| Fixed Responses. RESTful endpoints return predefined sets of data. Clients cannot request arbitrary fields, limiting the risk of over-fetching data but often leading to under-fetching or over-fetching. | Flexible Queries. Clients can specify exactly what data they need, reducing unnecessary data transfer. However, this flexibility can lead to over-fetching, where users retrieve more data than necessary or permissible. |
| Endpoint Overloading. Additional endpoints or query parameters are often needed to cater to specific data requirements, increasing the surface area for potential vulnerabilities. | Nested Queries. GraphQL allows nested queries, enabling clients to fetch related data in a single request. While powerful, this capability introduces risks if proper authorisation is enforced at only some levels. |
For RESTful APIs, the fixed nature of responses makes it easier to predict and secure data exposure, though the proliferation of endpoints can complicate access control management. In contrast, GraphQL’s dynamic queries necessitate stringent field-level permissions and continuous monitoring to minimise and control data exposure.
Injection Vulnerabilities
Injection vulnerabilities are a significant security concern for APIs, as they can allow attackers to execute malicious code or manipulate data. This type of vulnerability arises when an application improperly handles untrusted input, allowing attackers to inject their own commands into the system. These commands can then be executed with the same privileges as the application, leading to a range of malicious activities, from data theft to full system compromise.
| RESTful APIs | GraphQL |
|---|---|
| Traditional Injection Attacks. If user inputs are not properly sanitised, RESTful APIs are susceptible to attacks, such as SQL injection. The clear separation of data and commands in HTTP methods aids in mitigating some risks. | Complex Queries. The complexity of GraphQL queries, which can include deeply nested structures, increases the attack surface for injection vulnerabilities. |
| Parameter Manipulation. URL parameters and payloads can be manipulated to inject malicious data, necessitating robust input validation and sanitisation. | Resolver Logic. Injections can occur within resolvers if they improperly handle user inputs, such as directly incorporating user data into database queries without sanitisation. |
For RESTful APIs, established practices for input sanitisation and validation help mitigate injection risks, though developers must remain vigilant. GraphQL, however, requires additional caution in resolver implementation, ensuring all user inputs are sanitised before being used in commands or queries to prevent injection attacks.
Denial of Service (DoS) Attacks
Denial of Service (DoS) attacks aim to overwhelm an API's resources, rendering it unavailable to legitimate users. Understanding the specific vulnerabilities to DoS attacks for both RESTful APIs and GraphQL involves examining the number of endpoints and the complexity of queries. Each paradigm has unique characteristics that influence its susceptibility to these types of attacks.
RESTful APIs are designed around multiple endpoints, each representing a specific resource or action. This architecture provides clear boundaries for operations but also introduces several points that can be targeted in a DoS attack. Attackers can target specific endpoints with a high volume of requests, causing server resources to be exhausted. For example, repeatedly calling an endpoint that performs a resource-intensive operation can degrade performance or crash the server. Furthermore, some endpoints may involve complex operations, such as database queries or data processing tasks. These endpoints are particularly vulnerable to DoS attacks if they are not optimised or protected by additional safeguards.
Conversely, GraphQL’s flexibility can be exploited to create complex, resource-intensive queries that drain backend resources.
| RESTful APIs | GraphQL |
|---|---|
| Endpoint-Specific Load. DoS attacks can target specific endpoints, overwhelming them with traffic. Rate limiting and load balancing are effective measures to mitigate these attacks. | Resource Exhaustion. GraphQL’s flexibility can be exploited to create complex, resource-intensive queries that drain backend resources. Attackers can craft queries with high depth or breadth, leading to server overload. |
| Predictable Attack Vectors. The predictability of endpoint behaviour allows for straightforward detection and mitigation of DoS attempts. | Query Complexity. Evaluating the cost and complexity of each query adds layers of challenge to defend against DoS attacks. |
For RESTful APIs, rate limiting and identifying attack patterns are easier due to predictable endpoint usage. In contrast, GraphQL requires sophisticated query cost analysis, depth limitation, and rate limiting to prevent resource exhaustion and ensure robust defence against DoS attacks.
Best Practices for Securing GraphQL and RESTful APIs
Effective API security practices and general cybersecurity hygiene and awareness are paramount, and without the basics, maintaining a well-functioning, reliable application will be a very laborious task. Some common guidelines include.
· Regular Security Audits. Conduct periodic security audits to identify vulnerabilities and necessary improvements. This helps in planning future security spending and ensures continuous enhancement of your security posture.
· Proactive Security Measures. Take a proactive approach to security by implementing measures to prevent potential threats.
· Incident Response Planning. Develop a robust incident response plan to address and mitigate the impact of security breaches quickly.
· Regular Updates and Patch Management. Keep all components of the API infrastructure up to date with security patches and updates.
Education and awareness are important yet often overlooked aspects of API security. It is crucial to ensure your team is knowledgeable about secure coding practices and receives adequate support and training to prevent and avoid common security vulnerabilities. This investment in education and awareness should be a key component of your cybersecurity expenditure.
While there are foundational best practices for securing any API, such as regular security audits and proactive security measures, specific guidelines are necessary to address the unique challenges presented by GraphQL and RESTful APIs. Adopting these tailored practices not only helps prevent financial and operational disruptions but also protects your reputation from the fallout of data breaches.
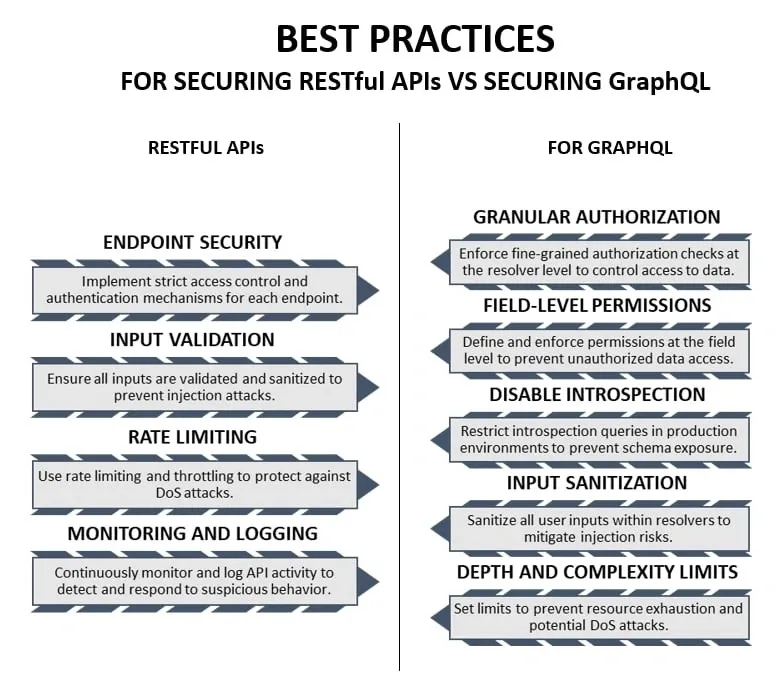
Remember: For RESTful APIs, implement strict access control and authentication mechanisms to ensure only authorised users can access specific resources and perform actions based on their permissions. Validate and sanitise all inputs to prevent injection attacks and use rate limiting and throttling to protect against DoS attacks. Additionally, continuously monitor and log API activity to detect and respond to suspicious behaviour.
For GraphQL security, enforce granular authorisation checks and field-level permissions to control data access and implement query cost analysis to manage resource impact. Additionally, turn off introspection in production, sanitise user inputs, and set limits on query depth and complexity to prevent injection risks and resource exhaustion.
In Conclusion
Choosing between GraphQL and REST begins with understanding your project's specific needs and requirements. This process extends to the security implications and strategies necessary to maintain its security posture. Both paradigms have strengths and weaknesses, and each offers unique security challenges.
For projects with heavy data usage and real-time requirements, GraphQL may be the better choice due to its ability to handle custom queries efficiently. Conversely, for applications where caching and established security practices are critical, REST might be more suitable. Experimenting with both can help determine which best fits your development workflow.
While both GraphQL and RESTful APIs provide powerful methods to build and interact with web services, they require different security approaches. RESTful APIs benefit from straightforward, endpoint-specific controls, whereas GraphQL’s flexibility necessitates more sophisticated security measures. By understanding and implementing best practices tailored to each paradigm, developers can secure their APIs against common threats, ensuring robust protection for their applications.
Expert testing is invaluable, and most mature cybersecurity frameworks require at least one yearly audit (e.g., AICPA SOC). Conducting proper root cause analysis (RCA) and addressing underlying problems in the remediation phase is crucial. Issues reported by InfoSec professionals should be thoroughly analysed and addressed. Additionally, development teams can acquire bad habits that span multiple applications or systems, so it’s important to recognise and correct these patterns.
For a deeper dive into common security vulnerabilities in GraphQL-based web applications, refer to WeakLink Security’s dedicated white paper, available via the form bellow. And, if you are ready to enhance the security of your web applications, get in touch with our team, which will happily collaborate with you to assess and secure your systems effectively.
Request White Paper
References
- Resty - Quick Start - Typeix. https://typeix.com/documentation/rest/quick-start/


